A new phishing campaign is targeting CFOs and finance leaders directly through LinkedIn. Attackers impersonate board contacts and send direct messages that appear to relate to executive activity. The link redirects through trusted domains including Google Search and Microsoft Dynamics, eventually landing on a fake Microsoft login page.
This attack chain used an Attacker-in-the-Middle (AiTM) kit, a CAPTCHA to block automated scanning, and multiple redirect paths through legitimate services. The goal was to hijack Microsoft 365 sessions and access finance platforms connected via single sign-on (SSO). This method has been observed in the wild targeting finance executives.
How LinkedIn phishing attack works, step by step
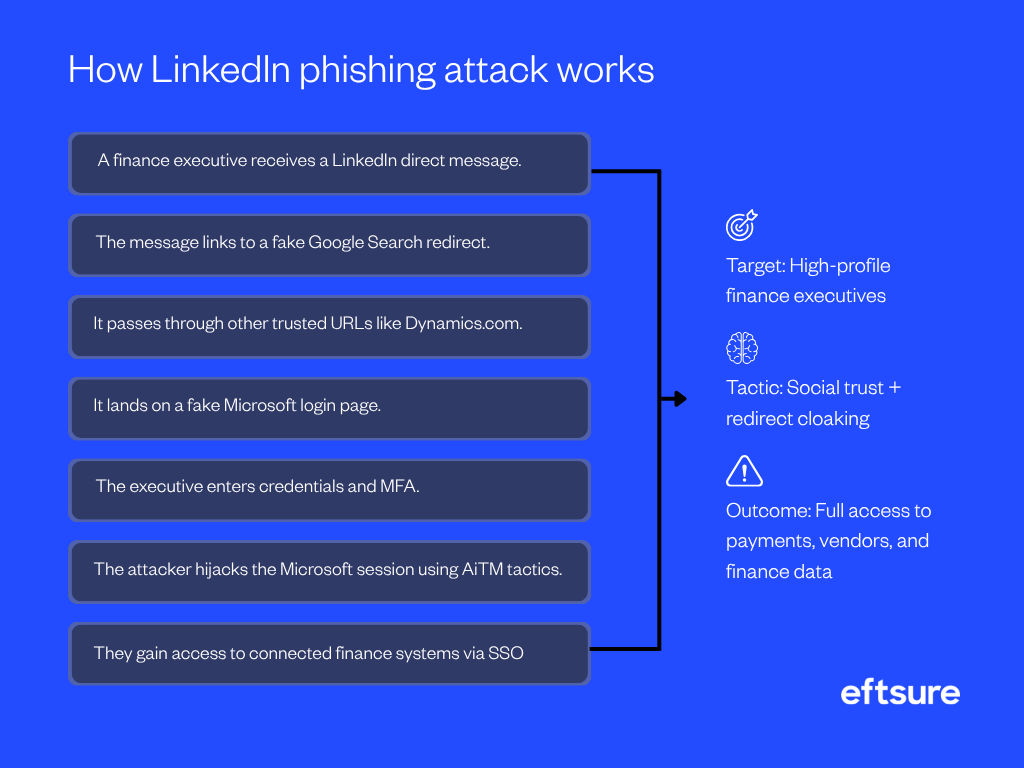
- A finance executive receives a LinkedIn direct message.
- The message links to a fake Google Search redirect.
- It passes through other trusted URLs like Dynamics.com.
- It lands on a fake Microsoft login page.
- The executive enters credentials and MFA.
- The attacker hijacks the Microsoft session using AiTM tactics.
- They gain access to connected finance systems via SSO.
This attack relies on social engineering and trusted-brand impersonation. The initial message appears legitimate, and the link paths look familiar.
Once hijacked, attackers operate with executive-level access. No password resets are triggered. No alert is raised. The session appears valid.
One stolen login. Full access to payments
With a hijacked Microsoft session, attackers can:
- Enter ERP or invoicing systems using trusted credentials.
- Modify supplier banking details.
- Approve or redirect payments.
- Disrupt reconciliation and reporting workflows.
- Bypass internal controls using a legitimate user profile.
This is not a theoretical threat. It is a direct path to payment fraud through executive compromise.
What finance leaders must do right now
- Train executives to treat LinkedIn as a phishing channel.
- Strengthen MFA with phishing-resistant methods like hardware keys.
- Audit which finance systems are exposed via single sign-on.
- Never process supplier changes from email alone. Enforce call-back verification.
- Prepare a credential compromise playbook that includes payment holds and supplier alerts.
How Eftsure stops payment fraud. Even after login hijack
Eftsure provides independent verification on every transaction. Even if a trusted login is compromised, fraudulent payments cannot go through.
With Eftsure, finance teams can:
- Validate supplier identity and banking ownership.
- Flag risky or suspicious changes before payment.
- Monitor transactions in real time.
Eftsure acts as the final line of defence when executive credentials are used to manipulate payments.
Protect your payments from hijacked logins
See how Eftsure prevents payment fraud, even if an executive login is compromised.







