A malicious insider – sometimes referred to as an insider threat – describes any person who uses their authorized access to a company's systems, resources, or data for malicious purposes.
Unlike the external threats posed by cybercriminals or hackers, malicious insiders have access to proprietary business information because they are employed by the company itself. In some cases, the malicious insider may also be a contractor, business partner, or former employee. Whatever the title, malicious actors share a common objective: to misuse or abuse their access privileges for personal or financial gain.
In a 2023 survey of more than 300 industry professionals, research firm Cybersecurity Insiders found that 74% believed insider attacks had become more frequent.
Motivations of Malicious Insider Attacks
Malicious insiders can be motivated by various means and their attacks can take many forms. Here are a few different types with real-life examples for each.
Unauthorized Access
Malicious insiders may exploit legitimate access privileges to obtain confidential or sensitive information, systems, and resources. Examples involving unauthorized access are some of the most well-known. One example is Edward Snowden, a former National Security Agency (NSA) contractor who leaked classified information to multiple journalists.
Data Theft or Breach
In this type, the malicious actor steals, sells, or deletes sensitive data, trade secrets, or intellectual property (IP). The intent here is to profit from proprietary information or harm the company by sharing it with competitors. In 2017, an employee of health company BUPA accessed the company’s CRM system to copy the personal details of more than 500,000 customers. The employee then deleted the information from the database and attempted to sell the personal records on the dark web.
Damage or Sabotage
This occurs when the malicious insider intentionally sabotages systems to cause operational disruptions, reputational damage, and financial loss. This may involve the use of malware or simply the deletion of critical files. In 2020, an ex-Cisco employee was jailed after deploying malware that deleted more than 16,000 user accounts and caused $2.4 million in damage.
Fraud
Fraud is a malicious insider technique often motivated by financial gain. Among other forms, it may involve embezzlement, insider trading, or the manipulation of financial records. In 2008, French bank Société Générale revealed that one of its employees had engaged in fraudulent trading activities. The employee took large, high-risk positions in European indices and concealed the trades via unauthorized and fictitious hedging transactions. Ultimately, Société Générale lost around $8 billion.
Espionage (Insider Threats)
On occasion, malicious insiders may represent external adversaries or competitors and take up employment with a company to steal its sensitive information. The insider threat may also originate from someone motivated by personal gain. Over eight years, a former General Electric (GE) employee stole over 8,000 files from the company. The employee, who convinced an IT admin to grant him access to the files, intended to use GE’s trade secrets to start a rival company.
How Can Malicious Insiders Be Detected?
Colleagues who routinely interact with the malicious insider are one of the best defenses since they are most likely to notice suspect behavior. Potential threat indicators are sometimes easy to spot. For example, the person may publicly hold a grudge against the company or one of their superiors. In other cases, indicators are less apparent. A malicious insider may:
Take on extra work with excessive enthusiasm.
Work at unusual times (such as accessing a network at 3 am).
Access unusual resources, or
Transfer abnormal amounts of data.
When detecting malicious behavior, it is important to assess intent. In other words, were the employee’s actions a deliberate attempt to damage the company or its assets? Or were they accidental?
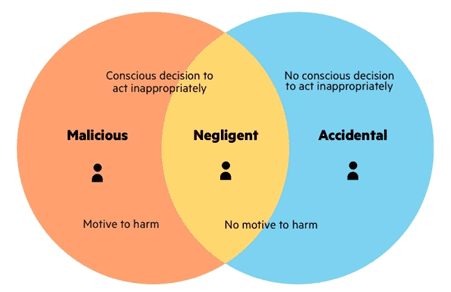
Some employees are deemed careless or negligent insiders because they unknowingly or unwittingly expose systems to outside threats. But each context is open to interpretation. The most clear-cut example of a negligent insider is an employee who falls victim to a cybersecurity scam and creates a vulnerability in the company’s systems.
Protecting Against Malicious Insiders
Most companies are well-versed in protecting themselves from external attacks. But how can they protect themselves against malicious insiders?
Protect Data Wherever It Is
An obvious point, but one that bears repeating. Data security should focus on areas where data lives – whether that be on-premise, in the cloud, or hybrid environments. In the context of malicious insiders, data leaks via email must be a priority. Some companies offer integrated, cloud-based solutions to prevent intentional leaks of IP and sensitive data.
Utilize Machine Learning
Machine learning (ML) applications can help organizations monitor the behavior of their employees and look for anomalies. Such applications fall within a category of security solutions known as User and Event Behavioral Analytics (UEBA). They establish a baseline for normal data access activity and then alert key personnel if abnormal access is detected.
Establish Multiple Layers of Protection
In addition to email security and ML-based user behavior analytics, there are various other focus areas for businesses. These include:
Database firewalls that block unsolicited backend database manipulation.
User rights management to identify instances of inappropriate, excessive, and unused privileges, and
Data masking or encryption, which obfuscates important data such that it becomes worthless to the malicious insider in the event it is extracted.
In summary:
A malicious insider is an individual who intentionally abuses access to a company’s systems, data, and resources for nefarious purposes.
Malicious insiders are invariably motivated by personal or financial gain. Different types of malicious attacks include espionage, fraud, unauthorized access, data theft, and damage or sabotage.
IT departments are typically capable of thwarting external attacks, but many are less prepared for the internal threat posed by a malicious insider. At the very least, the business should protect data wherever it lives, take advantage of user behavior analytics tools, and consider multiple layers of protection.
References




