Remote access trojan (RAT) malware is malicious software that permits cybercriminals full, unauthorized remote access to a victim’s computer.
Once installed, the malware allows attackers to control the infected system as if they had physical access. This enables them to monitor user behavior, steal data, and interfere with business operations without detection.
How Remote Access Trojans Are Used in AP Fraud
Remote access trojans are purpose-built for stealth and control. In AP departments where invoices, payments, and approvals are processed daily, a RAT can silently observe and then hijack transactions.
Once deployed, often as the result of phishing emails or malicious download packages, the attacker has administrative control over the compromised system. This means they can access financial platforms, alter payment details, and intercept email communications without alerting staff.
Specific RATs like Remcos and Agent Tesla have been used to extract information from finance teams. Common capabilities that enable this type of fraud include:
Monitoring user activity via screenshots, clipboard access, and file exploration to observe invoice and payment actions
Keylogging to capture usernames, passwords, and financial system credentials
Remotely controlling the infected machine to interfere with approval workflows or initiate unauthorized actions
Accessing email and financial software to alter communication trails or modify bank account details
Why Detection Is So Difficult
One reason RAT malware is so harmful is its ability to avoid detection. These tools blend into systems and operate in the background, often disguised as software updates, invoice attachments, or bundled with cracked applications and torrent files.
Once active, RATs may hide from the task manager, disable antivirus programs, and mimic traffic patterns to bypass intrusion detection systems. Some variants go further. They disable the webcam indicator light while recording, monitor user behavior to identify payment patterns, and even delete files to hide their tracks.
On Windows systems, attackers frequently exploit built-in operating system tools like PowerShell to carry out malicious activity without triggering alerts. Sophisticated RATs (such as this one from 2024) can also reactivate themselves after reboot and temporarily halt operations in sandbox environments to evade detection.
Perhaps most importantly, RAT infections remain undetected long enough that attackers can learn a company’s internal processes and strike at the opportune moment.
Why AP Teams Are Vulnerable
Accounts payable teams have direct access to a business’s cash flow. They process large volumes of high-value transactions and are often under pressure to do so quickly.
Other factors that make AP teams vulnerable include:
Frequent use of email-based approvals without multi-factor authentication
Broad administrative control across systems and platforms
Minimal monitoring of user behavior and device activity (especially if the malware mimics normal user activity)
Limited segmentation or least privilege access settings
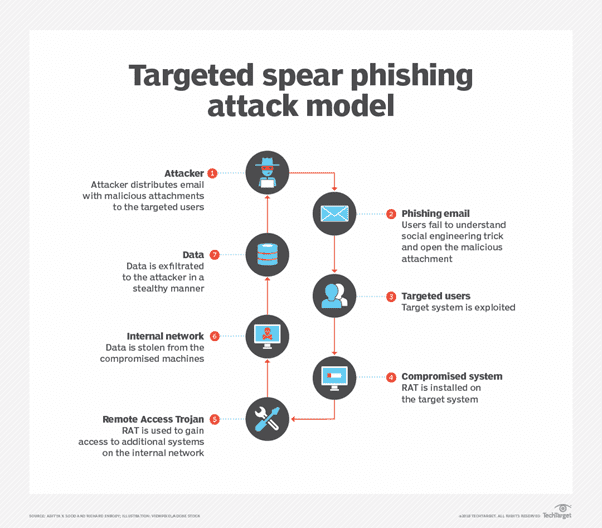
How RAT malware is delivered as part of a spear phishing attack (Source: TechTarget)
RAT Malware Case Study
In early 2024, Mexican financial institutions with revenue over USD 100 million were the victims of a random access trojan called Allakore RAT.
The RAT was distributed to key staff via sophisticated spear phishing or drive-by compromise attacks in the form of an MSI installer—a standard (and trusted) installation file used by Windows.
Phishing emails also incorporated links to harmless documents and naming schemas used by the Mexican Social Security Institute (IMSS) to add further authenticity to the scam.
Once executed, a small program first confirmed that the victim resided in Mexico before activating the malware.
In addition to remote access capability, Allakore RAT included other commands to commit bank fraud such as clipboard manipulation. This functionality enabled the malware to intercept and redirect funds based on copied transaction and cryptocurrency wallet details.
To conclude, let’s take a look at how (and why) the criminals selected their victims to maximize the odds of success:
IMSS reporting is a proxy for company size. In Mexico, businesses that report to the IMSS are typically medium to large enterprises with formal employees and payroll systems. They’re also more likely to process numerous financial transactions and store valuable data.
Higher-value targets, better return. Rather than cast a wide net, the attackers focused their efforts on companies with deeper pockets and more complex systems. These entities tend to have accounts payable (AP) departments, established vendor payment processes, and access to banking or cryptocurrency services.
More credibility, less suspicion. Employees at these firms engage in routine admin tasks like downloading invoices and HR files. A malicious MSI file disguised as an HR or payroll-related document is less likely to raise suspicion—especially when the IMSS file nomenclature adds credibility to the scam.
In summary:
RAT malware gives attackers complete control of infected systems and allows them to intercept payments, steal credentials, and manipulate financial workflows in real time.
Accounts payable teams are prime targets for various reasons. They manage high-value transactions and often lack advanced access controls or behavior monitoring.
The Allakore RAT case study demonstrates how threat actors use highly targeted, geography-specific malware to infiltrate systems. It also emphasizes the importance of training staff to recognize risks in seemingly routine file formats like MSI installers.




